NEWYou can now listen to Fox News articles!
Dating sites that bill themselves as discreet and private have often failed to live up to that promise. Take Ashley Madison for example, a dating website specifically marketed to people seeking extramarital affairs, which suffered a massive data breach in 2015. Hackers leaked the data of 32 million users, including personal information, emails, and financial details, leading to public outrage, lawsuits, and reported suicides.
Now, a dating safety app called Tea has suffered a breach of its own, compromising selfies, photo identification, and images from posts, comments, and direct messages within the app.
Sign up for my FREE CyberGuy Report
Get my best tech tips, urgent security alerts, and exclusive deals delivered straight to your inbox. Plus, you’ll get instant access to my Ultimate Scam Survival Guide – free when you join my CYBERGUY.COM/NEWSLETTER.
DIOR DATA BREACH EXPOSES US CUSTOMERS’ PERSONAL INFORMATION
What you need to know about the Tea data breach
Tea launched in 2023 as a U.S.-based “dating safety” app for women, requiring verification via selfies and government-issued ID. The ID requirement was phased out later that year. The app gained viral momentum in July 2025, reaching the top of the U.S. App Store and accruing millions of users
On July 25, users on 4chan discovered a publicly accessible Firebase storage bucket containing data of Tea users (via 404Media). A post reportedly exclaimed: “DRIVERS LICENSES AND FACE PICS! GET THE **** IN HERE BEFORE THEY SHUT IT DOWN!”
Tea later confirmed that the breach involved unauthorized access to a legacy database containing approximately 72,000 images, including 13,000 selfies and ID photos, and 59,000 images from posts, comments, and messages. These belonged to users who signed up before February 2024.
Tea’s leadership issued public statements confirming the image breach and claimed the data came from older systems not migrated to current secure infrastructure. Tea also stated that no email addresses or phone numbers were exposed and that only legacy users were affected.
New revelations from independent researcher Kasra Rahjerdi and reporting by 404 Media showed that the breach extended far beyond images as approximately 1.1 million direct messages (DMs) spanning from early 2023 through July 2025 were also exposed. These included highly sensitive conversations about abortions, cheating, phone numbers, meeting info, and more.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
In response, Tea disabled its DM system and took the affected messaging system offline. The company announced that it found no evidence of intrusion into other parts of its infrastructure.
CyberGuy reached out to Tea for comment but had not received a response by the time of publication.
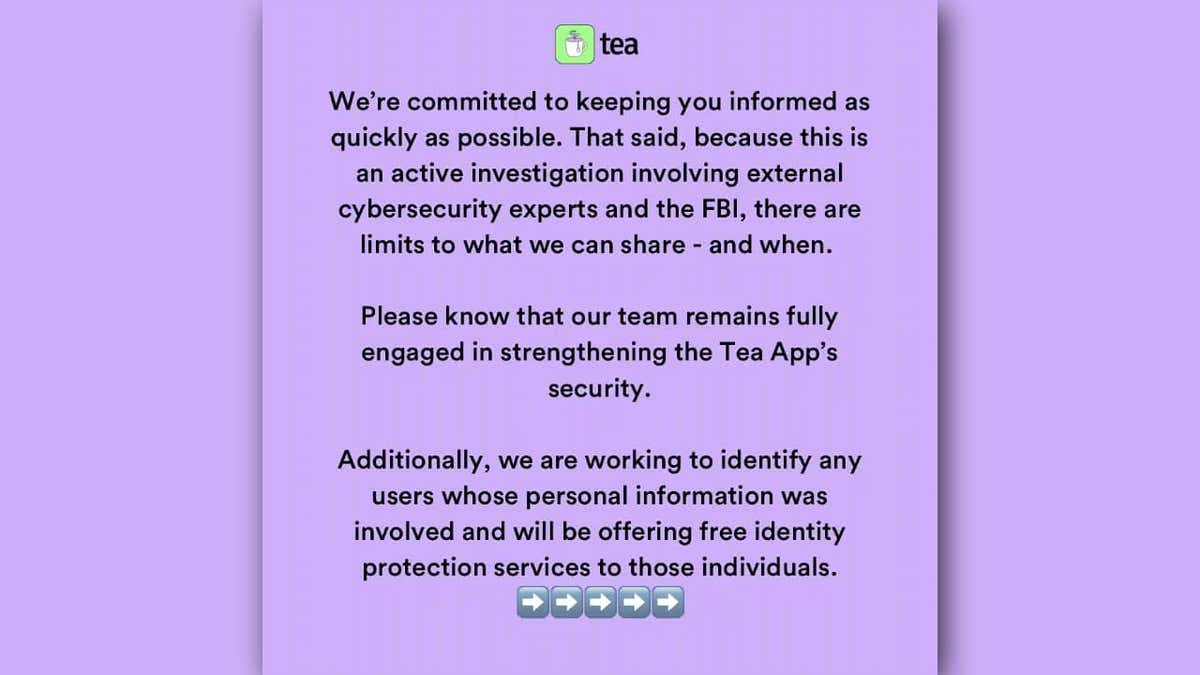
Tea app customer notice. (Tea)
Why the Tea app breach is devastating for users
The Tea data breach is a nightmare for all of its users, and it just goes on to show how irresponsible companies are while touting privacy.
Tea positioned itself as a safe space for women to share intimate experiences and then failed at the single most important promise it made, which is protecting that intimacy.
This wasn’t just usernames or email addresses. We are talking about government IDs, selfies, and 1.1 million private DMs containing confessions, relationship details, and deeply personal topics like assault and abortions. That’s the kind of breach you can’t walk back. Once those images and conversations are out in the wild, they are effectively permanent.
Tea wasn’t a generic social app. It marketed itself as a “dating safety” platform for women, meaning users had a reasonable expectation of higher-than-standard privacy protections.
These leaks hit a misogynistic forum first. Victims weren’t just exposed, they were immediately subjected to harassment campaigns, doxxing attempts, and having their faces and stories circulated without consent.

A woman using an app on her smartphone. (Kurt “CyberGuy” Knutsson)
6 ways you can protect yourself from Tea data breach
If you’ve ever used Tea or even just signed up, it’s important to take action now. Here are six steps to help protect your privacy and limit the fallout.
1) Sign up for identity theft protection
If your ID was part of the leak, you’re at risk of impersonation, and an identity theft protection service can help you stay safe. These services alert you to suspicious activity like new credit inquiries, account openings, or changes to your financial records, helping you act before the damage spreads.
See my tips and best picks on how to protect yourself from identity theft at Cyberguy.com/IdentityTheft.
2) Use a personal data removal service
Leaked selfies or names can end up on people-search sites or shady databases. A personal data removal service can help you remove all this personal information from the internet. While no service promises to remove all your data from the internet, having a removal service is great if you want to constantly monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time.
Check out my top picks for data removal services and get a free scan to find out if your personal information is already out on the web by visiting Cyberguy.com/Delete.
Get a free scan to find out if your personal information is already out on the web: Cyberguy.com/FreeScan.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
3) Change your passwords and use two-factor authentication (2FA)
Attackers often cross-reference usernames and reused passwords across the internet, even if your login wasn’t part of the leak. Updating your passwords and enabling two-factor authentication on all accounts is a basic but crucial defense. Consider using a password manager, which securely stores and generates complex passwords, reducing the risk of password reuse.
Check out the best expert-reviewed password managers of 2025 at Cyberguy.com/Passwords.
4) Be alert to phishing and blackmail attempts and use strong antivirus software
After high-profile leaks, it’s common for victims to receive threatening messages. Don’t respond. Don’t click links. Report the message and block the sender. If you feel unsafe, contact local cybercrime authorities or a digital rights organization.
The best way to safeguard yourself from malicious links is to have strong antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe.
Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android & iOS devices at CyberGuy.com/LockUpYourTech.
5) Check where your images are being shared
Use reverse image search tools like Google Images or PimEyes to see if your face has been posted elsewhere. If you find anything, document it. Report it to the platform and avoid engaging directly with whoever shared it.
6) File a complaint with regulators
If you believe your data was mishandled, you can file a complaint with:
- The Federal Trade Commission (FTC) at reportfraud.ftc.gov
- Your state’s attorney general or data protection authority
This adds pressure on the company to take responsibility and may help prevent future misuse of your data.
CLICK HERE TO GET THE FOX NEWS APP
Kurt’s key takeaway
It’s an absolute shame that a platform promising privacy and giving women a space to open up didn’t put in the effort to protect the data it was holding. If it were any other kind of app, this could still be contained. But one where people share sensitive information puts users in real danger. We’re already seeing people harass those whose data was leaked, and it will likely get worse from here.
Do you think apps that handle sensitive data should be held to stricter security standards? Let us know by writing us at Cyberguy.com/Contact.
Sign up for my FREE CyberGuy Report
Get my best tech tips, urgent security alerts, and exclusive deals delivered straight to your inbox. Plus, you’ll get instant access to my Ultimate Scam Survival Guide – free when you join my CYBERGUY.COM/NEWSLETTER.
Copyright 2025 CyberGuy.com. All rights reserved.

